How to configure SSH key-based authentication
Key-based authentication is strongly recommended for ssh logins, with the caveat that the SSH private key is passphrase protected and kept in a secure environment. The SSH public key is just that - public; it does not expose any information about the account or who has access to it. It cannot be used without the corresponding private key. However, the private key must be protected as it allows access to any systems that use the key pair for authentication. If the private key was generated without being protected by a passphrase, then possessing the key alone allows authentication. With an associated passphrase, both the key file and the passphrase must be known to utilize the key for authentication. Best practices are to use the private key only on a trusted system, such as a GFE laptop or known secure personal device.
Key-based authentication in PuTTY
PuTTY includes an application called PuTTYgen to create key pairs. Start PuTTYgen either through the Windows Start menu or from Windows Explorer.
Select Generate in the PuTTY Key Generator window. Move the mouse to create the random values used to develop the key, then enter the key passphrase. The key comment is a free-form text field used as a reminder on when/where the key was generated.
The default key type of RSA with length 2048 is adequate for account security, although the paranoid can increase the length to 4096. EdDSA is acceptable but none of the other choices should be selected.
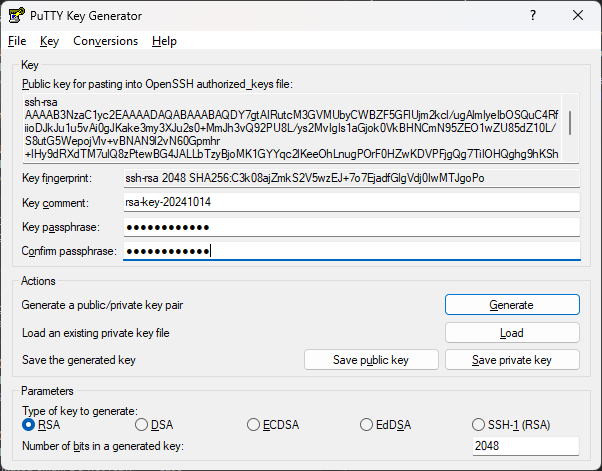
Select Save public key and Save private key to write the keys to disk on the laptop. These will be used by PuTTY when connecting to the server.
The public key needs to be copied to the FRCE head node.
Log in to FRCE using the standard password-protected SSH/PuTTY session
Create the SSH directory with mkdir ~/.ssh; chmod 0700 ~/.ssh. The top pane in the PuTTYgen window shows the generated public key. Select the text beginning with ssh-rsa and copy to the clipboard with ctrl-C.
On FRCE, create the authorization file with nano ~/.ssh/authorized_keys, enter ctrl-V to paste the public key. Use ctrl-x to save the file and exit. Set the permissions on the file with chmod 0600 ~/authorized_keys.
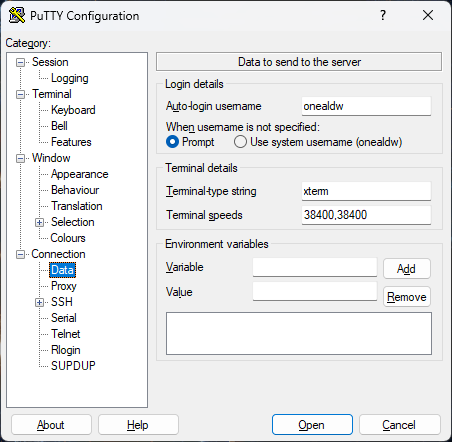
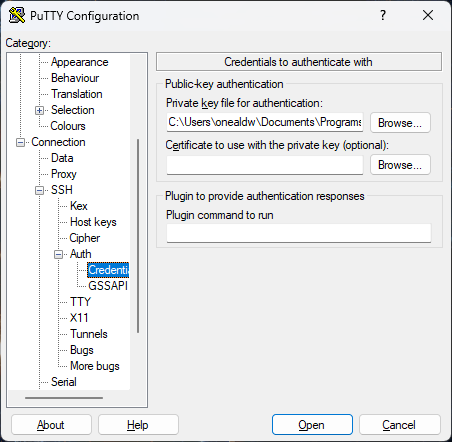
To configure the PuTTY client to use this key, open a PuTTY window. In the left pane, select Connection → Data. Enter your NIH username in the Auto-login username text box. Next select Connection → Data → SSH → Auth → Credentials and enter the path to the saved private key file.
Go back to the Sessions pane, select Default Settings, and click on Save.
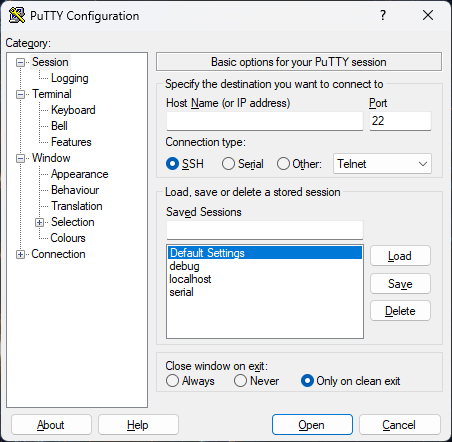
Test the process by logging into batch.ncifcrf.gov. If everything is configured properly, PuTTY will prompt for the passphrase to the private key and then log in the session with no further input.
PuTTY provides an application that can be started when the Windows session starts, that prompts for the private key passphrase once and then passes the private key on to PuTTY without needing further prompts. Outside sites that provide instructions include Digital Ocean and the WinSCP site.
Key-based authentication in MobaXterm
Generating an SSH key-pair in MobaXterm is virtually identical to the process used in PuTTY. Start the application and browse to Tools -> MobaKeyGen. This will bring up a window identical to that in PuTTYgen so follow the directions given for that application.
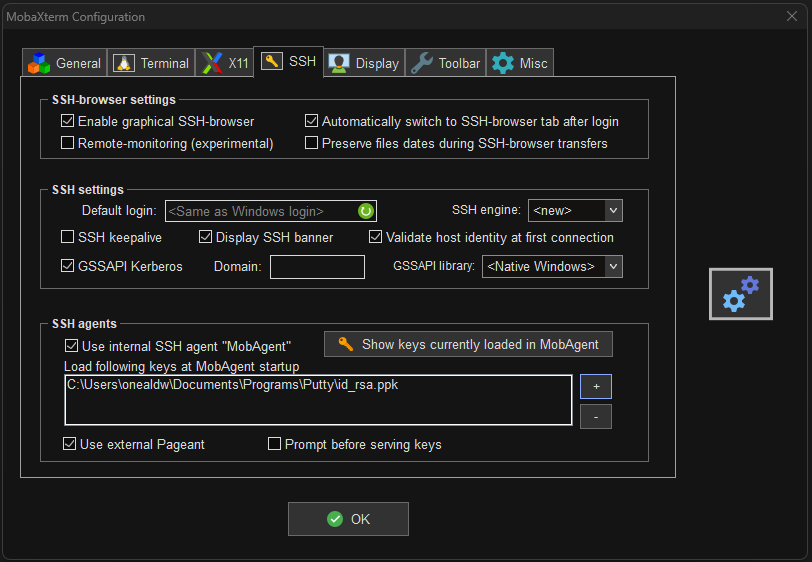
Browse to Settings -> SSH. Two options are generally useful. Choosing Use internal SSH agent after loading the saved private key will enable the the key specifically for MobaXterm. Alternatively, choosing Use external Pageant will use the PuTTY pageant utility. PuTTY will need to be installed to access this service. Instructions for configurating pageant are given above.
Key generation on Mac or Linux
Generating and using SSH key pairs is much simpler than on Windows.
$ ssh-keygen Enter file in which to save the key (/home/onealdw/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/onealdw/.ssh/id_rsa. Your public key has been saved in /home/onealdw/.ssh/id_rsa.pub. The key fingerprint is: SHA256:nsk5FN79E6POXckVOtyzMgHF3Sf8dJaQ1hNDREbtDyQ onealdw@fsitgl-head01p.ncifcrf.gov
As with the instructions for PuTTY, append the contents of id_rsa.pub to ~/.ssh/authorized_keys. No other changes to the ssh application are necessary.


